|
Microsoft Defaced, again!
Written by EGiovanni Delvecchio & Roberto Preatoni
(06/27/2007 )
Original
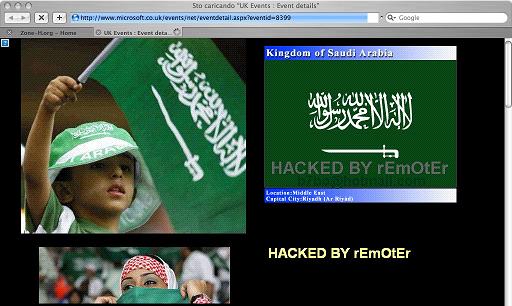
Very little time has passed from the last Microsoft defacement (Microsoft Technet), when yesterday Saudi Arabia crackers successfully compromised another Microsoft website: Microsoft.co.uk at the page http://www.microsoft.co.uk/events/net/eventdetail.aspx?eventid=8399.
At the time being, the defacement is still up and running even though not every browser will be capable to show it as too many users are trying now to load the hacker's injected CSS (Cascading Style Sheet) located on an external host (h.1asphhost.com) which now has is suffering slow response time.
By analyzing the HTML source code of the defaced page we can see some "extra" HTML code:
"<link xhref=http://h.1asphost.com/remoter/css.css type=text/css rel=stylesheet>".
The technique used by the attacker to deface Microsoft's page is probably based on a kind of SQL flaw (sql injection). In fact, after a short investigation we noticed how the V2 parameter passed to the PreRegister.aspx script, allows to execute both Cross Site Scripting attacks (www.microsoft.co.uk/events/net/PreRegister.aspx?eventID=p8399&v2="><script>alert(/XSS/)</script>) as well as SQL injection attacks, as you can deduct from the debug error message generated by the application.
Most probably, the attacker exploited the site by means of SQL injection to insert the HTML code "<link xhref=http://h.1asphost.com/remoter/css.css type=text/css rel=stylesheet>" in a field belonging to the table which gets read every time a new page is generated. To discover the name of the table the attacker might have queried the database trying to read the system table "SysObjects" or even the INFORMATION_SCHEMA.TABLES view. We are just speculating here as the DBMS is most probably a MS SQL Server.
The result after the defacement is this one:
|