|
Microsoft.com defaced
Written by Marcelo Almeida (Vympel)
(05/03/2007 )
Original
Few days ago, the website Microsoft IEAK was victim of a defacement. The website promotes the “Internet Explorer Administration Kit”, a toolkit that allows to “deploy and manage Web-based solutions,” and to “learn how to tailor a custom browser to meet customers' needs,” the website says.
The attacker is known by the handle Cyber-Attacker (cyb3rt), he is from Saudi Arabia, and he is not new to such activities. He is the one who carried out to a XSS attack against one of Zone-H staff members, stole his administrator password and by this mean defaced Zone-h English website.
As reported by the attacker, the page contains a SQL Injection flaw in the Login field, by which he got to execute arbitrary sql commands and inject the html content that altered the page of Microsoft IEAK web site....
Flaws of SQL Injection are in general as common as ' OR ' =', and thanks to the improvements in technology and in web coders’ skills, cyber attackers could learn lots of things on SQL , and subsequently they perfected their ability to provoke headaches to web admins…

Image of the defacement to http://ieak.microsoft.com
Many people think that such attacks can be led just for pages based on ASP, and for log-in forms. Actually, this kind of attack can be carried out against any page/source type, be it ASP, HTML, PHP or CFM: the only difference is the method. Whenever there is a mistake in SQL queries, there could be an exploitable flaw for cyber criminals.
The only solution for admins is to work hard in collaboration with coders, revising the source code to patch any visible mistake that could generate problems in the future.
But since the possibility to perform a “complete revision” of the source code is infrequent, due to a huge amount of web pages source code to revise, another solution is needed: for instance, the adoption of modules for Apache as mod_security and of .ht access to restrict the execution of SQL strings into URL and activating magic_quotes in the PHP configuration.
In Windows Servers, administrators can use filters directly on their we pages. Such filters can check users input and help, this way, administrators to prevent digital attacks.
One prevention-method used by these filters, is based on disabling of warnings messages, because the apparition of similar warnings are a sort of signal that helps the attacker to get to the website’s database or to the table/column where he is going to make the attack.
Even today, Cyb3rt attacked a long list of web pages, including the website of the popular Security Company Kaspersky Labs. see the image below:
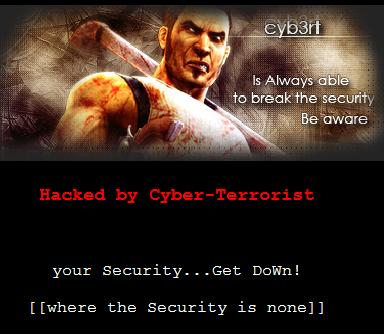
Image of the dafacement to Kaspersky Labs
|